
Public Domain
By Joseph Mazur
I have no idea what Signal is. I don’t care what Signal is … All I can tell you is it’s just a witch hunt, and it’s the only thing the press wants to talk about, because you have nothing else to talk about. Because it’s been [sic] the greatest 100-day presidency in the history of our country.
– Donald Trump, NBC News (29 March 2025)
Secrets are the pillars of warfare security. Leaks picked up by adversaries can destroy a military strategy and vastly alter world history. That vast altering happened just over a century ago. One careless breach in messaging could cause a country to weaken its standing among allies. In this, I forward examples of how careful military leaders must be with their words, targets, dispatches, and communiqués. Though the most recent scandalous incident of insecure messaging had some luck, it lost allied intelligence fidelity, a reliance that is difficult to restore.
At the end of the summer of 1944, the 20th infantry division of the US Third Army, under the command of General Walton Harris Walker, had established a bridgehead on the Seine near Fontainebleau. The Germans were in retreat, fleeing Paris. My father and a British soldier (named Winslow, as I recall) who somehow was embedded with the Third Army, had the intrepid job of furtively tailing German PanzerKampfWagen tanks armed with 37mm L46 guns. The Panzers’ massive steel treads cut Allied communication wires spooled out along muddy, boot-sucking terrain that once had been fields of red poppies. My father’s job was to splice wires soon after being cut, so that George Patton’s Third Army could communicate with Omar Bradley’s Twelfth and Bernard Montgomery’s Twenty-first. In mid-August, Bradley gave the Germans an escape route out of Paris to save Patton’s outnumbered troops from a major assault. My father was justly forever proud to say that his brave splicing saved hundreds of American and British lives.
The Twenty-first Army Group controlled ground force operations with Polish, Dutch, Belgian, and Czech forces, but communications came through effective lines connecting operations involving supplies and reinforcements. Radio communication was too insecure on battlefields. Airwaves today are far less private than they were 81 years ago. So now, in March 2025, why were 18 people miles apart on a group chat revealing US war plans on cell phones easily hacked by adversaries? Military officers know not to use their phones if sharing operational details of a potential strike; that is basic military knowledge.
If a country wants isolation, it’s easy to accomplish it through intelligence breaches.
My readers know and understand that my column “Understanding War” rarely brings in specific wars unless there are examples that convey an understanding of the nature of wars and why they happen, being careful to not wander too far out of my depth. So please excuse, and stay with me, for this segue to an example of a particular military blunder that attaches itself to reasons for why such blunders can start and envelope intelligence agency disconnects to the point of breaking alliances apart, a point that can turn away any one of those friendly countries that militarily supported the United States in the Iraq and Afghanistan Wars. If a country wants isolation, it’s easy to accomplish it through intelligence breaches. But, as has happened in the past, a single decoded secret military message can change the path of history. Those not knowing that should not have any access to military secrets.
We do not have to be military geniuses when evaluating whether the information shared on Signal was classified. The evidence is clear, according to The Atlantic’s detailed publication of the back-and-forth texts sent at 10:15 ET, 15 March 2025, two hours before American airmen were in flight in their F-18s to attack Yemen:

The Director of National Intelligence, Tulsi Gabbard, told the United States House Intelligence Committee, “There were no sources, methods, locations or war plans that were shared. This was a standard update to the national security cabinet that was provided alongside updates that were given to foreign partners in the region.”[2] European intelligence agencies – like everyone who has seen the evidence with a sense of truth – hesitate to share their most precious hard-earned secrets and prefer to ramp up their own highly protected sources.
Intelligence! What does that word mean? In military use, the context is the ability to collect valuable strategic information. Dictionaries claim it to be “the ability to acquire and apply knowledge and skills.” Both definitions entangle the two words, ability and knowledge. So, one would expect the United States Director of Intelligence to be “able” to appraise the difference between unsecured “valuable strategic information” and applicable “knowledge and skills.” For that matter, with 18 people on the Signal chat – including the Secretaries of Defense, State, and the Treasury, along with the director of the CIA – you would expect that at least one of those members of the inner sanctum of national security would have been smart enough to know that chatting about a secret military attack via Signal on a cell phone is dangerously wrong. But none had enough intelligence to halt the communication.[3] Was it a lapse in judgment? Likely! Or by an unlikely worse lapse in judgment, it could have been a diversionary scheme to stealthily punt power on its way to patrimony – create a scandal to divert the media from the stirring episodes of covert deviltries that would otherwise leak.
Why am I bringing this up when most of the world has learned about this incompetence through the news that has not let this go? The news of this Signal ignorance is constant for good reason. The answer is that one dumb move in military communications that does not take secrets seriously can bring half the world down militarily. When Pete Hegseth, Secretary of Defense, says, “THIS IS WHEN THE FIRST BOMBS WILL DEFINITELY DROP, pending earlier ‘Trigger Based’ targets,” gives the exact time of the drop two hours earlier, and later says, “Nobody’s texting war plans, and that’s all I have to say about that,” the crisis inflates to a collapse of allied trust. And trust is the basis of details of military accomplishments.[4]
That abandonment of taking secrets seriously has put the United States in the unfriendly position of being a soft ally not to be trusted with hard-earned information that could be compromised and could expose agents or battle plans to interception. In addition, several European allies say, “Our relations with the United States are over and … we can no longer depend on America.”
So, America seems to feel it can go it alone, if it needs to, without foreign intelligence. Example: The U.S. Secretary of Defense, a former television presenter who approved “swift and unrelenting” air bombings of remote Yemen mountains and deserts with “sublime ahistorical clumsiness” seemed to be not only without a realistic strategy to – as Trump hoped – “annihilate” the Houthis who for 18 months have been attacking ships in the Red Sea, but also without intelligence or expert advice. The U.S. Air Force did assassinate a Houthi commander. But history and expert foreign policy advisers tell us that “air power rarely wins wars, and the Houthis have the advantage of a remote, mountainous hinterland where much of their arsenal is probably safe from harm.”[5] David Frum, a staff writer at The Atlantic, says, “Americans have tried these narrow and selfish methods before. They ended in catastrophe. History does not repeat itself: The same mistakes don’t always carry the same consequences. But the turn from protector nation to predator nation will carry consequences bad enough.”[6]
Yes. But history does repeat itself in widening three-dimensional spirals. News of today can mimic those of fifty or a hundred years before. The same catastrophes recur because historic information eventually passes into bleary memory voids. And now, after a month of scandal, Hegseth comes into the news for a repeat performance on a cell phone, again on a second (or possibly the third or fourth) Signal group chat-sharing of sensitive, if not classified, information with his wife, brother, and lawyer.[7] Does Hegseth know that his “personal phone number, used in Signal chat, could have been found in a variety of places on social media and fantasy sports sites”?[8] It seems funny yet dumb. Sports sites? Gosh, David Gardner, Chief National Correspondent for The Daily Beast, agrees with The New York Times, saying that Hegseth’s number was on “WhatsApp, Facebook, Airbnb, a fantasy sports site and reviews left for a plumber and a dentist,” exposing national secrets to anyone listening in through a significant lapse in security protocols.[9] Though luck had saved the F-18 pilots, his future blunders seem to be aiming for a military catastrophe that will soon come to the Pentagon theater.
Could a wartime security breach perturb and ravage a longtime future of humanity?

Public Domain
The most careless military communication of all was that of the now-famous Zimmermann telegraph, an encrypted Western Union message sent to Mexico suggesting that, if Mexico were to side with Germany in WWI, the winning side would award Mexico three American states that once belonged to Mexico – Texas, Arizona, and New Mexico.
It was the biggest mistake of the twentieth century, because it opened a series of possibilities that would have drastically changed a hundred years of history.
At that time, Arthur Zimmermann, a German foreign minister, decided that because the British had cut the transatlantic cables, his only path of trans-Atlantic communication would be by encrypted messaging sent by telegraph. It was the biggest mistake of the twentieth century, because it opened a series of possibilities that would have drastically changed a hundred years of history. Had Zimmermann acted more wisely, he would have sent his message through a safer route by an established secure courier. It would have been entirely possible that the United States would not have entered the war on the side of the Allies, and therefore opened the possibility that Germany would have either won that bloody war or accepted a truce. Had either happened, it’s likely, according to many historians, that the fascists of the early 1930s would have had a hard time to collapse the German Weimar Republic. Imagine how history could have unfolded without convincing arguments blaming Jews, homosexuals, people of color, or communists. Germany, before WWI, was a constitutional monarchy, an empire endowed with a strong economy, leaving Mussolini aspirants for the world to learn its lesson on how dehumanising fascism could be.
According to the U.S. National WWII Museum, roughly 3 percent of the world population would not have died by direct or war-related causes. That’s close to 70 million who might have lived longer lives. But America didn’t enter the war to save lives or combat the growth of fascism. Rather its decision to join was influenced by Britain’s Room 40, a secret cryptanalysis agency in the Old Admiralty Building in London, that intercepted and deciphered the Zimmermann telegram on its way to the president of Mexico.[10] Its contents were then passed on to the British Foreign Secretary, Arthur Balfour, who showed the decoded message to the U.S. Ambassador to Britain, Walter Page. From Page it went to Secretary of State Robert Lansing, who showed it to President Woodrow Wilson. Five days later, the Associated Press released the telegram contents to newspapers across the country. “And so,” David Kahn wrote in his book The Codebreakers, “it came about that Room 40’s solution of an enemy message helped propel the United States into the First World War, enabling the Allies to win, and into world leadership, with all that that has entailed. No other single cryptanalysis has had such enormous consequences. Never before, nor since, has so much turned upon the solution of a secret message.”[11]
Most spy communications are successful, so we never hear about them. In contrast to the Zimmermann blunder, I bring up a masterful spy story that few people know, though it happened at roughly the same time as the Zimmermann telegraph.

Public Domain
At 2:08 am, Sunday, 30 July 1916, six months before the Zimmermann telegraph interception, New York and New Jersey residents were awoken by a series of massive explosions that sent shock waves in all directions as far as 90 miles, demolishing an entire island in New York Harbor. In Jersey City, the epicenter, and almost all of Manhattan south of Times Square, windows blew out. It was the most powerful explosion in the New York / New Jersey area in history – before 9/11, that is. So why is it that almost nobody knows about it, even older folks born and raised in New York? The explosions repeated in sequence until daylight. The story is extraordinary but let us return a few months before that disquieting Sunday. To tell the story briefly, we begin with Emanuel Voska, a stonemason born 4 November 1875, in Kunta Hora, a silver mining town in the Central Bohemian Region of the Czech Republic (Czechia). Voska was an unsung hero, an unknown to most Czechs, yet one who was most responsible for the founding of Czechoslovakia.
When war broke out on 28 July 1914, Voska cultivated a group of spy agents nested inside and out of the German embassy in New York City. Every night for two years, those agents stealthily steamed open diplomatic pouches, forwarding contents on German plans of sabotage to agents of the United States Bureau of Investigation (later to be called the FBI). Details were discovered of German U-boats close to the east coast of the US and particularly upsetting messages to and from German agents with sabotage plans for exploding railcars loaded with ammunition ready to be shipped to Russia for the war in Europe. Specific decoded facts divulged that underwater saboteurs were about to detonate ships of explosive cargo loaded from Lehigh Valley Railroad boxcars stationed at the Black Tom Island rail docks. How do I know about this? I was 16 when I first came across a book hidden in a crevasse of a monolith, Spy and Counterspy. From that, I learned about Voska’s spy ring. Through all the years of Voska’s espionage activity, no member of the ring was ever discovered.
When military secrets were secure, and when they were not
Sometimes military plans are shared between allied countries, sometimes not. Here are four examples.
1. Pagers sold to Hezbollah
On 17 September 2024, many members of Hezbollah were injured, and some were killed, by remote-controlled explosions of their newly acquired pagers and walkie-talkies. Concealed explosives were in batteries of devices secretly manufactured by a Hungarian firm and dispensed to Hezbollah commandos, allegedly by unsuspecting Iranian agents. Mossad was involved with three shell companies and Aman (the Israeli intelligence service). Yoav Gallant, Israel’s defense minister, accredited “excellent achievements, together with the Shin Bet, together with Mossad.” The significance was that the explosive material inside the pagers’ lithium batteries was undetected by both the border patrols and Lebanese security. Imagine how tight communications must have been for three countries (Taiwan, Hungry, and Israel) to secretly manipulate events involving thousands of explosive devices to reach Lebanon and explode on a specific day without a single communication leak.
2. Assassination of Osama bin Laden
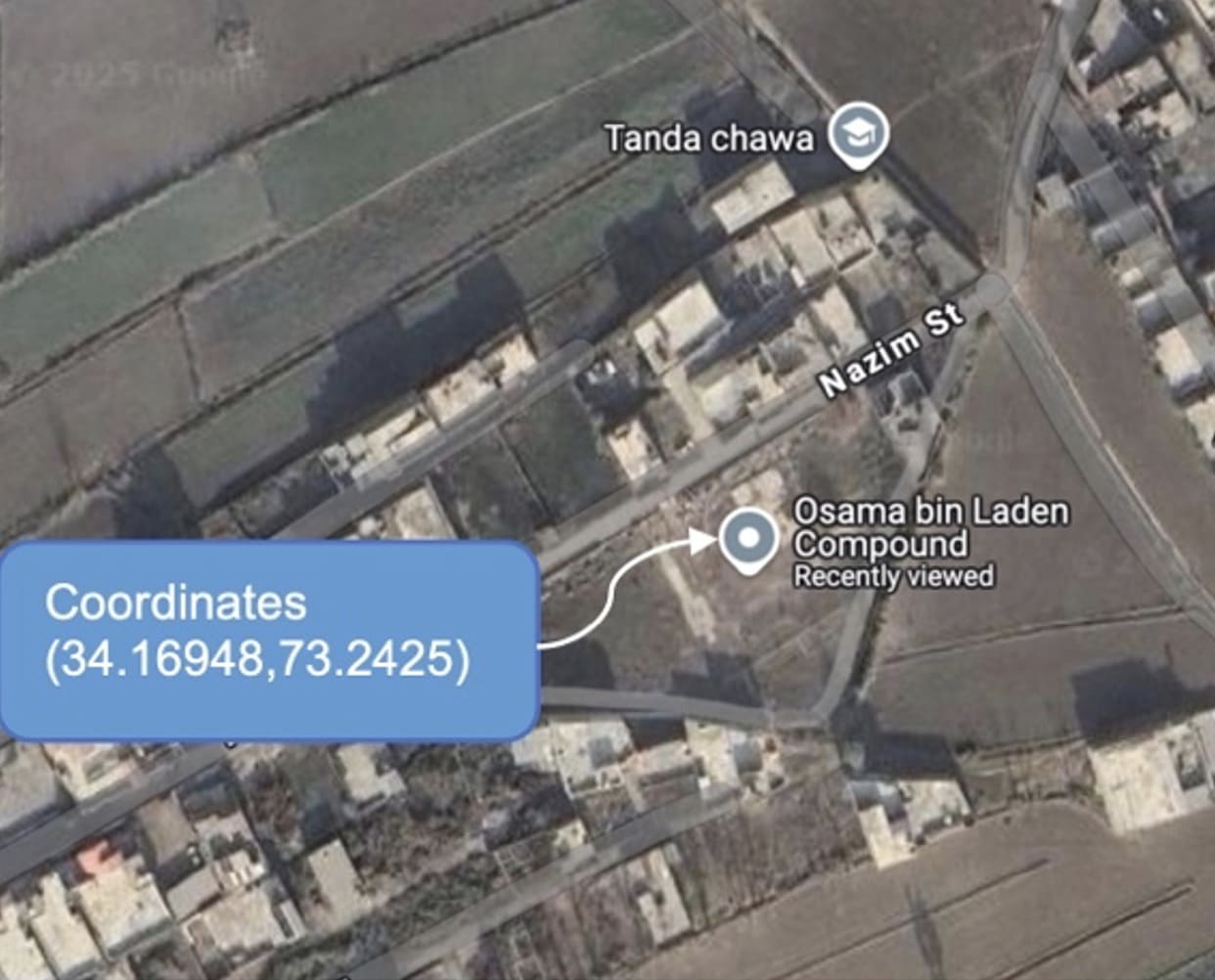
A careless Osama bin Laden’s courier is a case of insecure communication that led to assassination. It didn’t take long for CIA agents to find bin Laden when his aids used cell phones to communicate. Phones of terrorist groups are always monitored, but in that instance, intelligence operations agents got connected to bin Laden’s personal courier. That courier picked up his phone to receive a call, and in that instant, the long search for bin Laden was over; U.S. intelligence traced the phone’s receiver precisely to Bilal Town, Abbottabad, Pakistan, coordinates (34.16948,73.2425). The assassination was coordinated and implemented with the Secretaries of Defense, State, and the Treasury, along with the director of the CIA and military personnel of the highest ranks – Barack Obama’s national security team. They were either in a Sensitive Compartmented Information Facility (SCIF) or the White House Situation Room (also a SCIF), watching in real time the assassination of the most wanted terrorist.
The group in the photo at the beginning of this article is watching in real time Navy Seals attacking Osama bin Laden’s compound in Abbottabad, Pakistan. The mission, from entry to exit from bin Laden’s compound, took just 38 minutes. It was a Navy Seal precision operation moving carefully through the compound, room to room, floor to floor, all accomplished by extraordinary intelligence. A culmination of years of intelligence work built inside sources, partly because phones, pagers, and computers were forbidden to be near his compound. Bin Laden was aware that the U.S. National Security Agency (NSA) was searching the airwaves for phone chatter connected to him. By chance, in the spring of 2011, the NSA established signals connected to bin Laden’s courier, which exposed the geographical coordinates of the compound. During subsequent development plans to get bin Laden, information was not shared, even with foreign intelligence communities, including the closest counterterrorism allies – Britain, Canada, and Australia.
3. Assassination of Russian generals
More than a dozen Russian generals died after they used their mobile phones at the beginning of the 2022 Russian invasion of Ukraine.[12] That is an extraordinary number and a huge upset for whatever prospects Putin had for a quick takeover of Ukraine. Retired four-star General David Petraeus quipped that Ukrainian troops “picked them off left and right.”

Wikipedia Commons
We don’t know for sure why so many commanders were targeted and killed. Experts speculate that the Russian military communications lines were not secure, since Ukrainian intelligence units were able to spot Russian invaders through their mobile phones. When tens of thousands of Russian troops were waiting for more than a month at the Ukrainian border, not knowing why they were there and what next, they spent a great deal of time on their cell phones calling home and texting friends. They did not disclose their coordinates, but just using their phones permitted foreign intelligence agencies to spot their phones with five-foot precision.
A secondary problem was the Russian plan of placing 20 generals in day-to-day tactical operations, preparing combat missions in the initial invasion. Aside from the loss of generals, close to 7,000 Russian troops were killed in the first three weeks of the invasion.[13] They were relying on ERA, a Southeast Asian PR network that was not as secure as they thought, according to Christo Grozev, an investigative journalist working for Bellingcat (an investigative journalism group working in the Netherlands), who investigated the deaths of the Russian generals.[14]
When Bellingcat intercepted a phone call, two Russian Federal Security Service (FSB) officers responsible for counterintelligence based in Ukraine asked their boss about the safety of using the ERA system. “The boss says Era is not working. Era is a super expensive cryptophone system that [Russia’s defense ministry] introduced in 2021 with great fanfare. It guaranteed [to] work ‘in all conditions’. Idiots tried to use the Era cryptophones in Kharkiv, after destroying many 3G cell towers and also replacing others with Stingrays.”[15] A Stingray is a cell site simulator that imitates and surveils cell towers to catch a mobile subscriber’s identity, locate phones, and intercept messages.
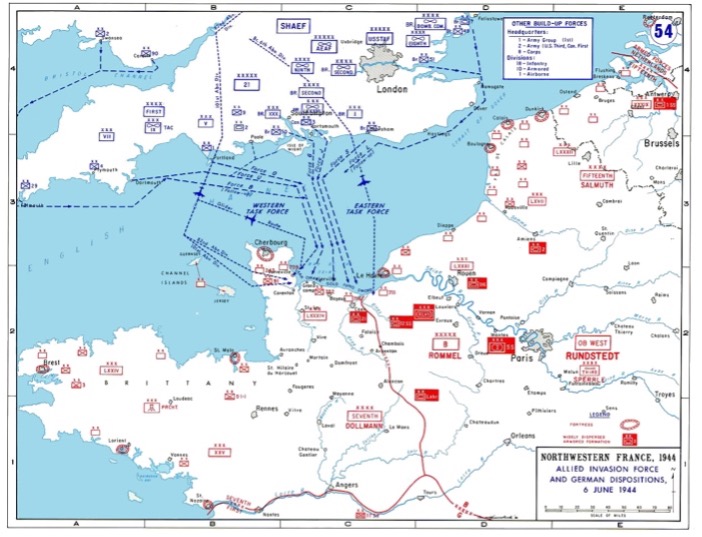
4. D-Day, Normandy landings
WWII D-Day communications between troop commanders were astounding examples of secrecy. On 6 June 1944, the German commanders believed that the Allied invasion from across the English Channel would be from Dover to Pas-de-Calais because 1) it was the shortest sea path, just 50 miles, a third the distance from Portland to the Normandy coast, and 2) the Germans were getting false chatter from intelligence. Codenamed Operation Neptune is still considered the largest military operation in history. See the photo of the landing and imagine how many commanders were involved in secrets that held tight for four months. Could that be done today?

Allied Expeditionary Force, London, 1 February 1944
Four months before D-Day invasion.
Public Domain
As you look at the photo on the left, you see an enormous number of ships, trucks, and troops under the guidance of landing operations held secretly for months without a pinhole leak. Granted, 80 years ago, there were few options for leaks, unlike today’s communication possibilities.
Public Domain
Now, on to spy satellites and their vulnerabilities that tell us why warfare security matters
Even with today’s advanced technology, miscommunication, or insecure messaging risks of cyber-snooping, satellite systems have improved security to extend the safety of military synchronization and coordination. They have a long way to go to have iron-tight blockages of eavesdropping. Take Starlink. Is it a secure system for military communication, classified or not? That’s the big question to be answered by a serious investigation. The answer is clear: no satellite communications network should be used for relaying classified information, because airwaves are involved. Outside a SCIF, there is no assurance that some adversary is not listening.
The U.S. Department of Defense military communications – for ships at sea and bases around the world – goes by way of a constellation of satellites, including the old Defense Satellite Communication System (DSCS) replaced by the Wideband Global SATCOM system (WGS), Wideband Gapfiller Satellites (WGS), Advanced Extremely High-Frequency (AEHF) satellite communications, and at least a dozen others. Take AEHF, for instance. Lockheed Martin built it to serve several countries, including Canada, Netherlands, and the UK, to provide secure links for “military commanders transmitting sensitive information in contested areas.”[16] So far, It is probably the most secure system available for general military use; yet, even at that high frequency and impressive performance, it could be vulnerable to interception, and manipulation. Every satellite communication system, including the most sophisticated military systems, has some vulnerability. None are as secure as a SCIF, an enclosed spy-proof area with walls lined with acoustic baffles that block audio snooping. The Situation Room in the White House is one such area. Radio waves and loud music within and outside the walls prevent sounds from escaping within. No one without top-secret security clearances, including any general or congressional delegate, is permitted to enter. Those who do must surrender all electronic devices beforehand.
Defense Intelligence Agency (DIA) specializes in military communication.
We hardly hear about this U.S. agency that employs 17,000 career civilians and expert analysts, half of whom serve in various covert positions throughout 140 countries, many in U.S. embassies, and many others in secret places surveilling any military intentions of legitimate governments and non-state players such as paramilitary forces. We might consider them spies – they are, of course – but equipped with surveillance tools to collect and analyze any chatters of foreign military intelligence. DIA is, in other words, a military and counterintelligence spy agency watching and collecting threatening details of information, both big and small, including “capabilities and intentions; proliferation of weapons of mass destruction; threats of international terrorism; international narcotics trafficking; and defense-related foreign political, economic, industrial, geographic, and medical and health information” to relay them to the U.S. Department of Defense and other appropriate government officials.
DIA has had its troubles with counterspies who infiltrated the agency. While successfully recruiting spies, some were working against DIA to leak classified information to the KGB, China’s Ministry of State Security (MSS), Libya, and the intelligence agency of Cuba (G2). They were allegedly double spies who caught drifts of classified information. Still, in the 64 years since its founding, there were no inadvertent leaks – not one – in that enormous agency.
With that many people working top secret, it could have been impossible to avoid leaks through Russian agents caught sending secrets to Moscow and Cuba.
Spying goes back to wars of ancient history; however, in the early Cold War years, militaries relied on relatively sophisticated intelligence and surveillance with numerous slip-up leaks that called for a tighter intelligence operation. The British Secret Intelligence Service (MI6) started in 1909 and grew to involve 15 analysts before WWI began. That low-budget operation continued and managed a successful spy / saboteur ring in Germany throughout the First World War and into the Second. It now employs 3,544. Most countries involved in that war had some ramshackle organizations monitoring sabotages and spying. By WWII, intelligence operations became far more seriously implemented. The British-US Communication Intelligence Agreement (BRUSA) at Bletchley Park, working on Ultra, the codename for cryptographic intelligence, employed over 10,000 by 1945. With that many people working top secret, it could have been impossible to avoid leaks through Russian agents caught sending secrets to Moscow and Cuba.
Unlike the UK, during WWII, the U.S. had no extensive intelligence agency. Multiple offices, such as the Office of the Coordinator of Information, later called the Office of Strategic Services (OSS), were relatively small, with staff numbers close to 2,000. As the war progressed, that number doubled, and by the war’s end, staff numbers were close to 35,000. Under the National Security Act of 1947, the OSS morphed again to become the Central Intelligence Agency (CIA), a centrally controlled body that we recognize as one that carries intelligence secrets in almost every country.[17] It now employs 21,575.[18] Those early agencies have had leaks of secrets but, again, none that we know of from errors of methods and rules about conducting espionage.
The Signal chat message of a war plan attack on Yemen scandal on 15 March 2025 had been in the news for a month before slowly evaporating to make news of other scandals involving the Trump administration that distracts with breaking news designed to diminish stories of its blunders. News must be new to keep the public reading or listening. Otherwise, news flops.
So, what must happen before the world suffers from inept military intelligence leadership? First, the public must understand that, in Hegseth’s case, messing with intelligence is calculated to distract from experimental ideologies that favor patrimony. Second, in a democracy, even one that is not perfect, incompetence risks catastrophe, so the public must stand firm in protest to bring consequences to lawlessness and moral misbehavior, with a buck-ends-here responsibility of leadership. When any nation, especially any of the most militarily powerful, settles for an unfit defense secretary whose specialty is kowtowing to his political allegiance, its path leads to imminent threat. In Hegseth’s particular case, a short-term consequence will be the loss of trust from friendly nations or a catastrophe hard to predict and repair. Yes, the news media on his incompetence is still with us to keep the public interested, but it will soon become a bore. Then what?
About the Author
 Joseph Mazur is an Emeritus Professor of Mathematics at Emerson College’s Marlboro Institute for Liberal Arts & Interdisciplinary Studies. He is a recipient of fellowships from the Guggenheim, Bogliasco, and Rockefeller Foundations, and the author of eight acclaimed popular nonfiction books. His latest book is The Clock Mirage: Our Myth of Measured Time (Yale).
Joseph Mazur is an Emeritus Professor of Mathematics at Emerson College’s Marlboro Institute for Liberal Arts & Interdisciplinary Studies. He is a recipient of fellowships from the Guggenheim, Bogliasco, and Rockefeller Foundations, and the author of eight acclaimed popular nonfiction books. His latest book is The Clock Mirage: Our Myth of Measured Time (Yale).
Follow his World Financial Review column at https://worldfinancialreview.com/category/columns/understanding-war/. More information about him is at https://www.josephmazur.com/
References
[1] The list includes the Secretaries of Defense, State, and the Treasury, along with the director of the CIA.
[2] https://www.politifact.com / factchecks/2025/mar/26/pete-hegseth / fact-checking-pete-hegseths-false-statement-that-n/
[3] https://www.defensenews.com / news / pentagon-congress/2025/03/26/obviously-classified-experts-say-hegseth-chat-leaks-invited-danger/
[4] That first chat is under investigation by the acting inspector general of the Defense Department
[5] https://www.theatlantic.com / international / archive/2025/04/bombing-houthis-trump-yemen-irsael/682353/
[6] https://www.theatlantic.com / magazine / archive/2025/01/trump-foreign-policy-isolation/680754/
[7] https://www.nytimes.com/2025/04/20/us / politics / hegseth-yemen-attack-second-signal-chat.html
[8] https://www.nytimes.com/2025/04/25/us / politics / pete-hegseth-phone-signal.html
[9] https://www.thedailybeast.com / pete-hegseths-personal-signal-chat-phone-number-is-all-over-the-internet/
[10] https://www.archives.gov / publications / prologue/2016/winter / zimmermann-telegram#:~:text=On%20February%2010 per cent20a%20British,during%20a%20February%2023 per cent20meeting.
[11] David Kahn, The Codebreakers: The Story of Secret Writing (New York: MacMillan, 1968) p 297.
[12] https://foreignpolicy.com/2022/03/21/russia-generals-dead-ukraine/
[13]https://web.archive.org / web/20220316225152/https://www.nytimes.com/2022/03/16/us / politics / russia-troop-deaths.html
[14] Naturally, Christo Grozev is on the Russian government’s “wanted list.”
[15] https://www.datacenterdynamics.com / en / news / ukraine-russian-militarys-own-encrypted-phones-impacted-after-destroying-3g4g-towers-allowing-comms-to-be-intercepted/
[16] https://militaryembedded.com / comms / satellites / military-communications-capacity-evolving-rapidly#:~:text=The%20capacity%20and%20capabilities%20of,common%20life%20cycles%20of%20products.
[17] https://www.nps.gov / parkhistory / online_books / oss / chap1.pdf
[18] https://web.archive.org / web/20100324152925/https://www.cia.gov / news-information / featured-story-archive / ohb-50th-anniversary.html
#Military #Intelligence #Future #Trust #Allies